Windows FTP Server with SFTP and FTPS






BPFTP Server has the ability to operate as a Windows System Service aka SERVICE-MODE (HOWTO).
This is essentially, the same as the normal GUI-MODE that you are used to seeing when you login to the computer and run the application, however it’s running under Session-0 (Windows System Service) and all GUI operations are hidden. This can make it more difficult to diagnose issues, as the software can only respond via the Windows Event Viewer (start, view) and the BPFTP Server Log (Settings -> Logging -> Settings -> “Saved Log-File Location”).
But, why is it not responding or is stuck at 100% ?!?!
I don’t immediately know the answer to this, the software doesn’t have any known problems which would cause this.. so we need to look at the environment, conditions and logs coming back from the software. It’s possible that there’s a network share that isn’t responding (the most likely issue), it’s also possible you’ve encountered an issue, in either case, we need more information…
When encountering a problem with running in SERVICE-MODE, it’s important to start breaking down the problem:
[table id=80 /]
[table id=79 /]
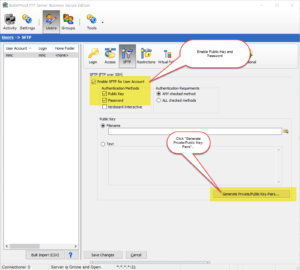
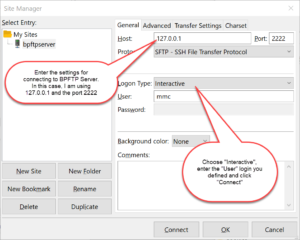
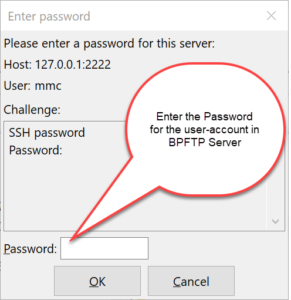
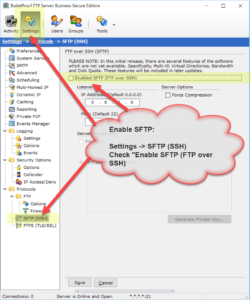
As of version 2018.0.0.40, BulletProof FTP Server supports SFTP aka FTP over SSH in the Secure Edition of the product.
Enabling SFTP for a given User-Account simply requires the toggling of the feature for the user-account, and specifying the authentication method. The two methods of authenticating are via Public-Key, Password or both. Optionally, you can specify that the authentication must happen via the keyboard.
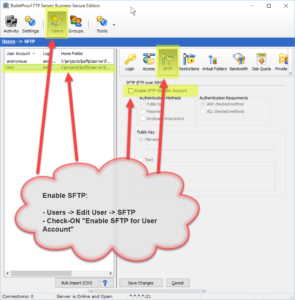
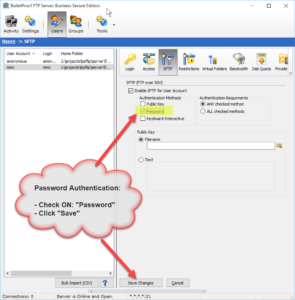
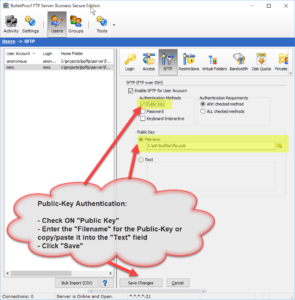
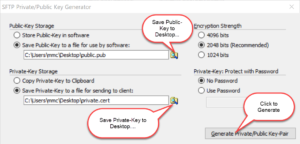
As of version 2018.0.0.40, BulletProof FTP Server supports SFTP aka FTP over SSH in the Secure Edition of the product.
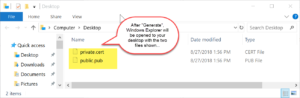
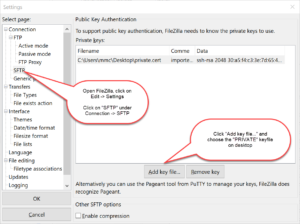
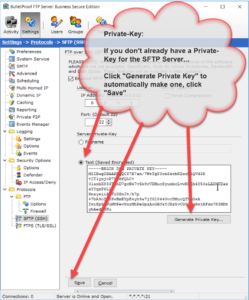
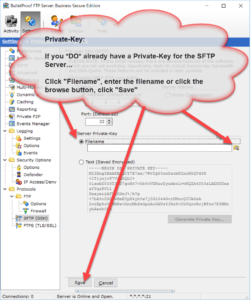
Enabling SFTP is very simple and only requires a Private-Key. The Private-Key can be loaded via a file or text which has been copy/paste’d into the software (NOTE: text keys will be stored encrypted in the software).
In some Windows configurations, it might be necessary to enter the license-code via the command-line. Specifically, in Windows Server where “Internet Explorer Enhanced Security” is turned on (More Info: here, here, here, here and here). When IE ESC is turned on, you’ll need to turn it off; this is because the dialog-box that appears for entering your registration code uses the IE WebKit and as a result the links won’t work correctly.
However, you don’t have to disable IE ESC, you can also enter it via the command-line:
1) Start -> Run -> "cmd" (enter)
2) c:
3) cd "C:\Program Files (x86)\BulletProof FTP Server"
4) Working with a license-code that looks like...
Name:John Doe
Key:00012X-8d7DJF2-6F323F-JVQBUA-8DJF3F-28RR4E-02Z6PC-ZXG37G-QBFDH2-NPDPBM-9XS9D9-MPH56G
Enter the following command:
bpftpserver.exe QUIETREGISTER John Doe 00012X-8d7DJF2-6F323F-JVQBUA-8DJF3F-28RR4E-02Z6PC-ZXG37G-QBFDH2-NPDPBM-9XS9D9-MPH56G
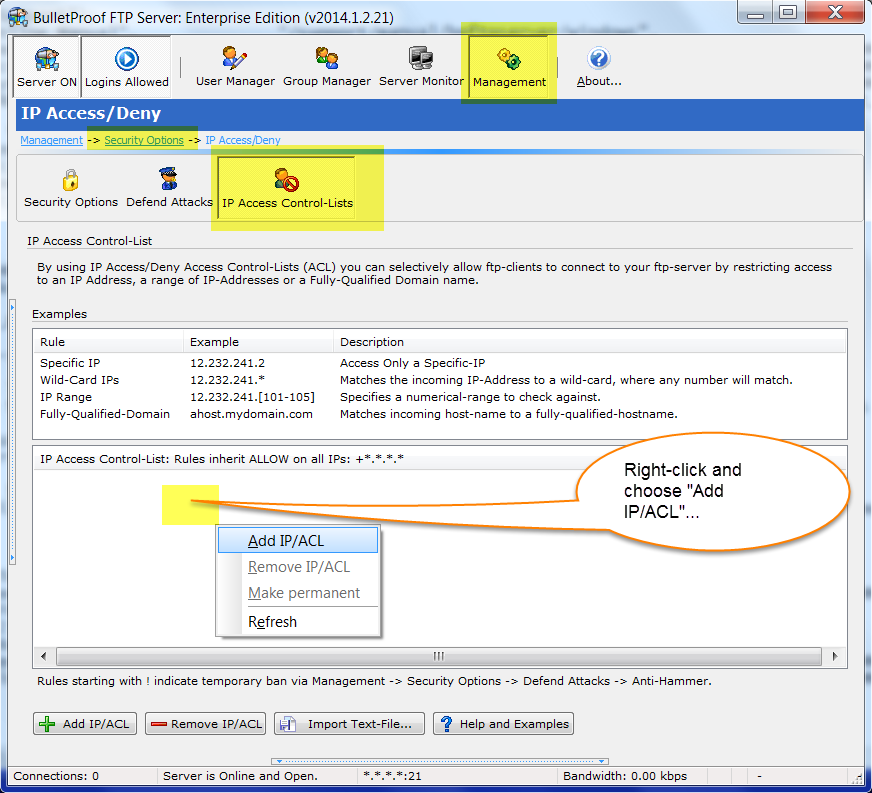
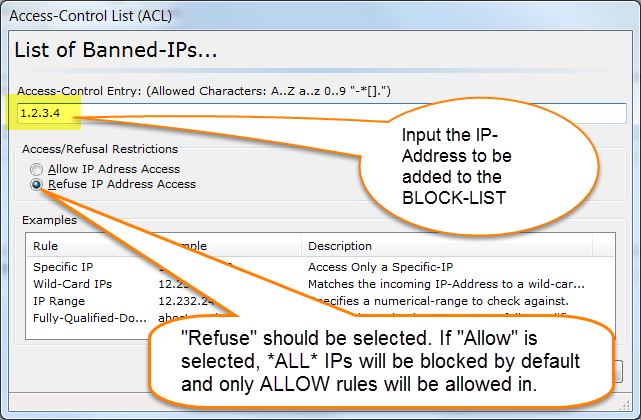
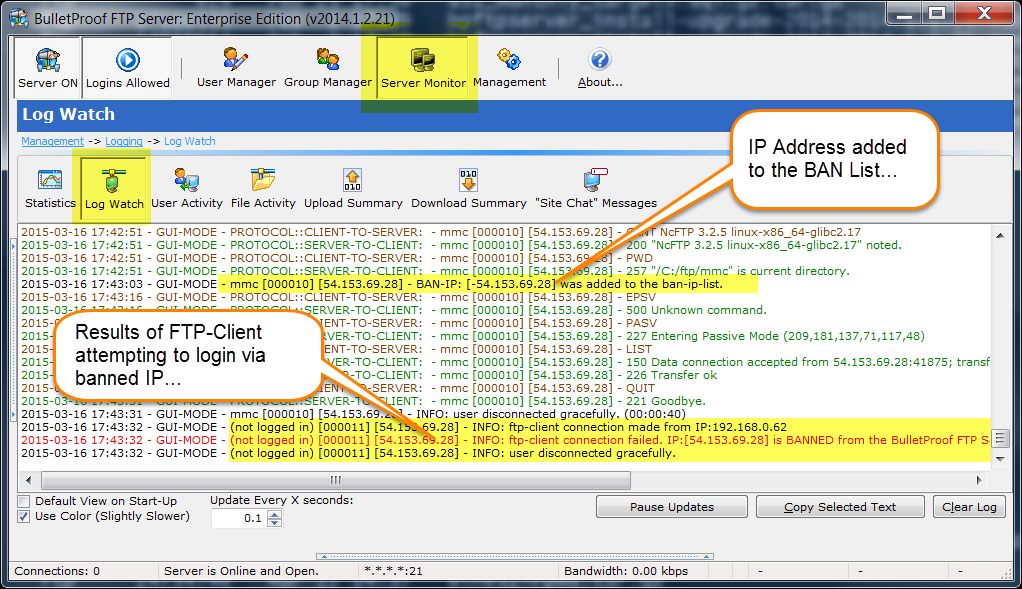
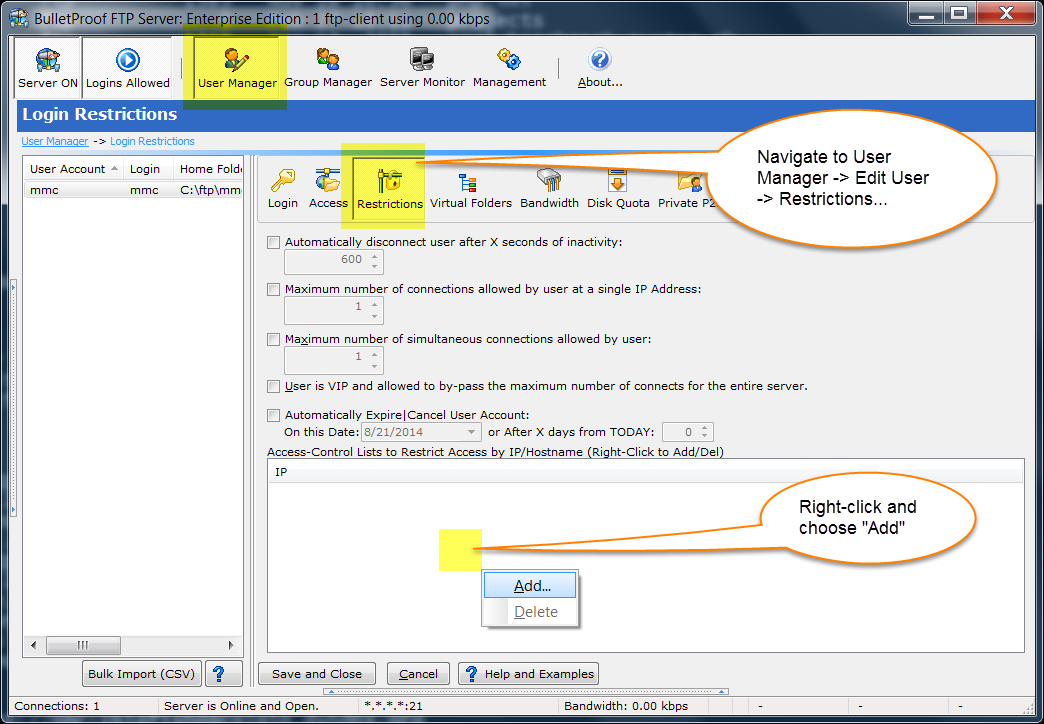
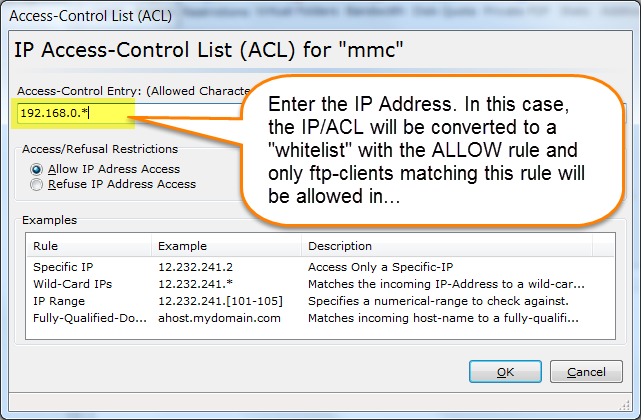
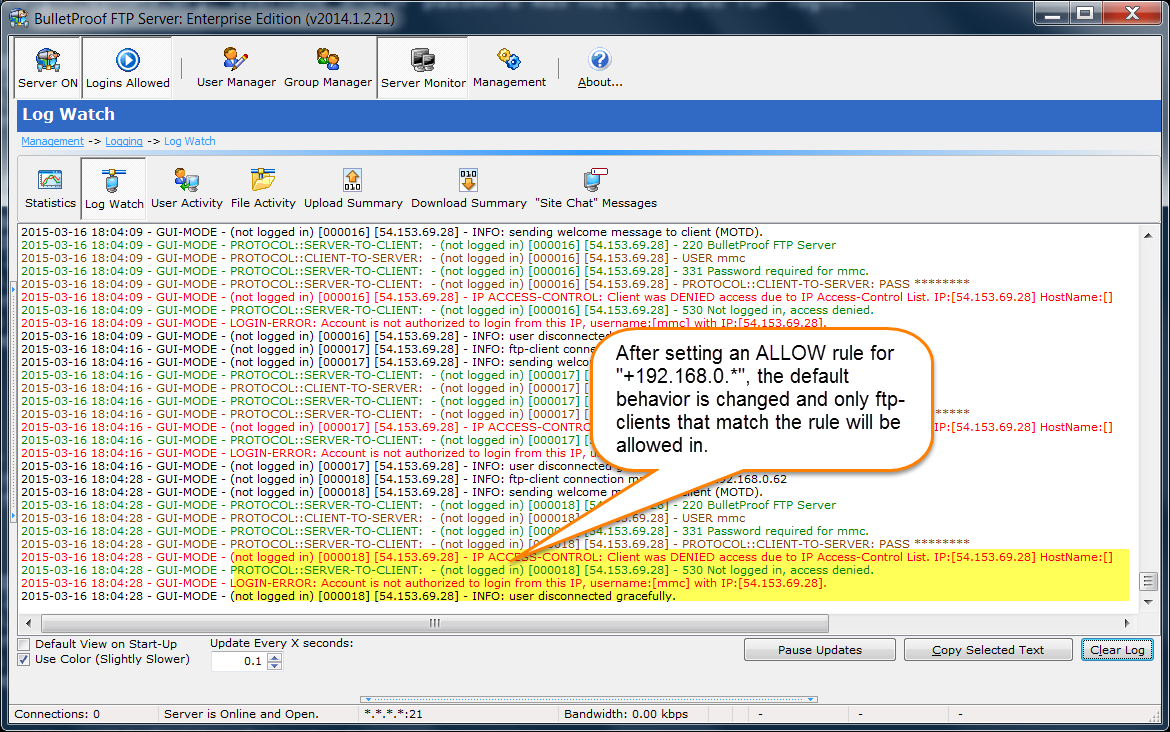
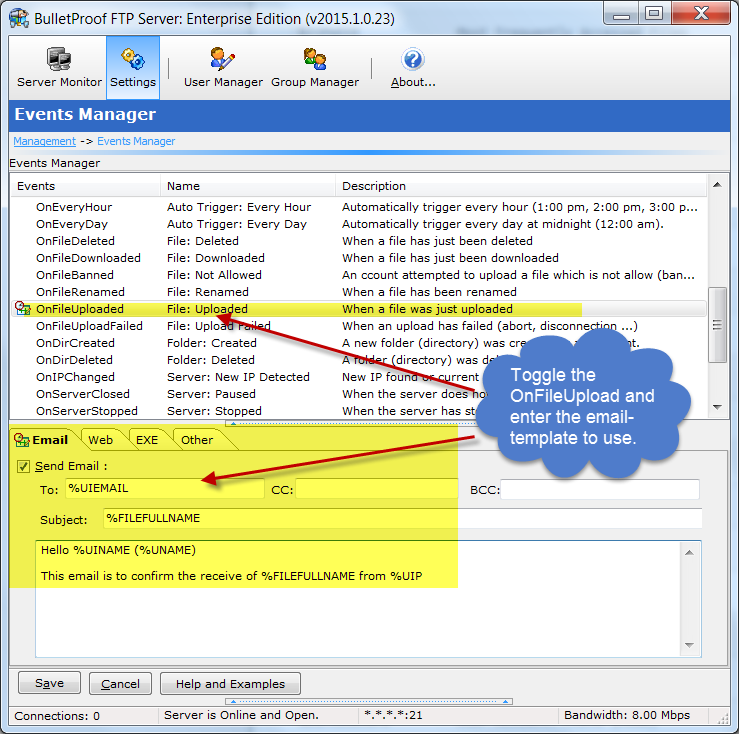
For a list of %VARIABLES that you can use in your email template, please see the following URL:
http://blog.builtbp.com/2015/02/feature-event-scripting/