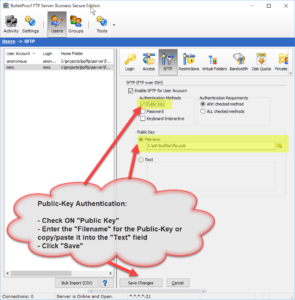
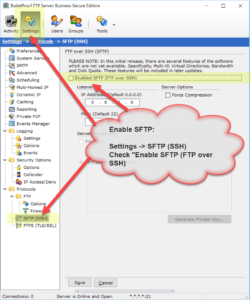
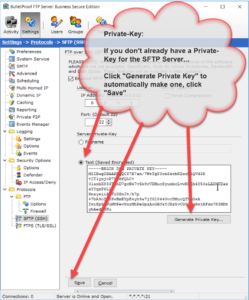
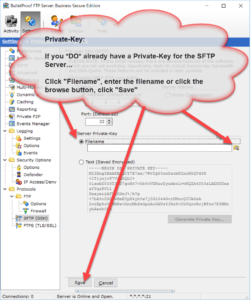
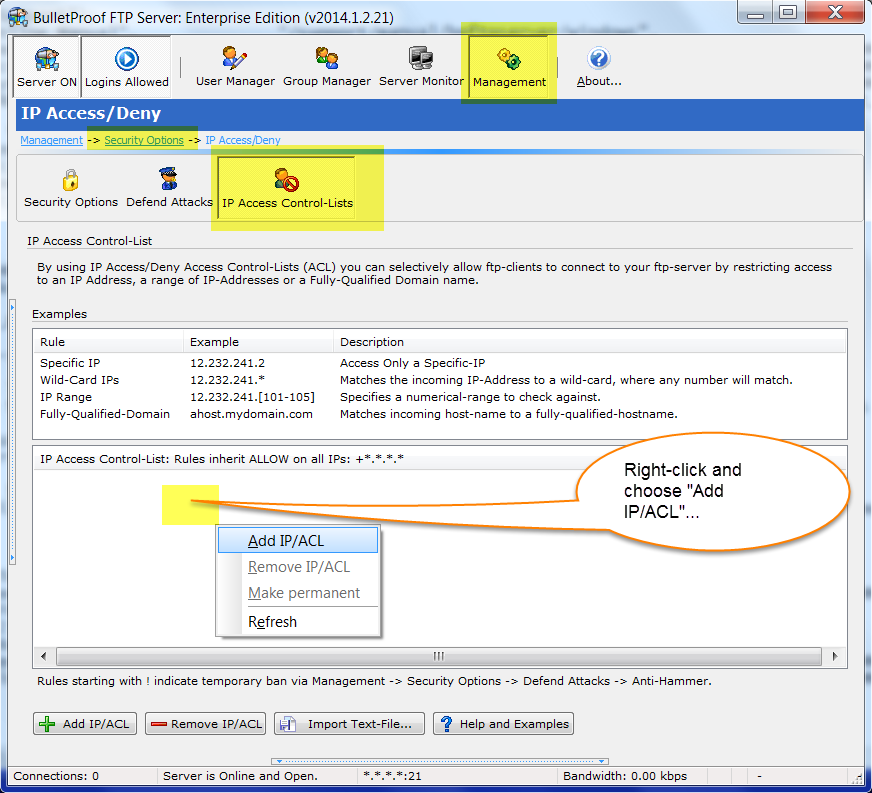
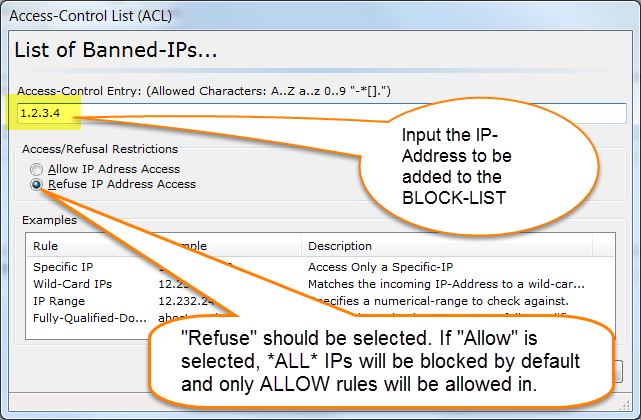
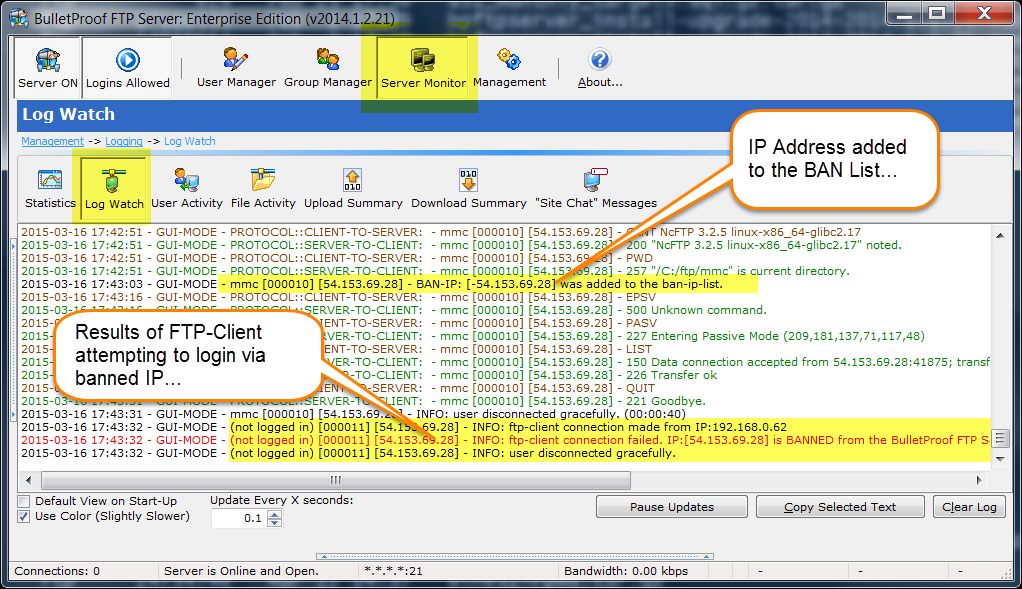
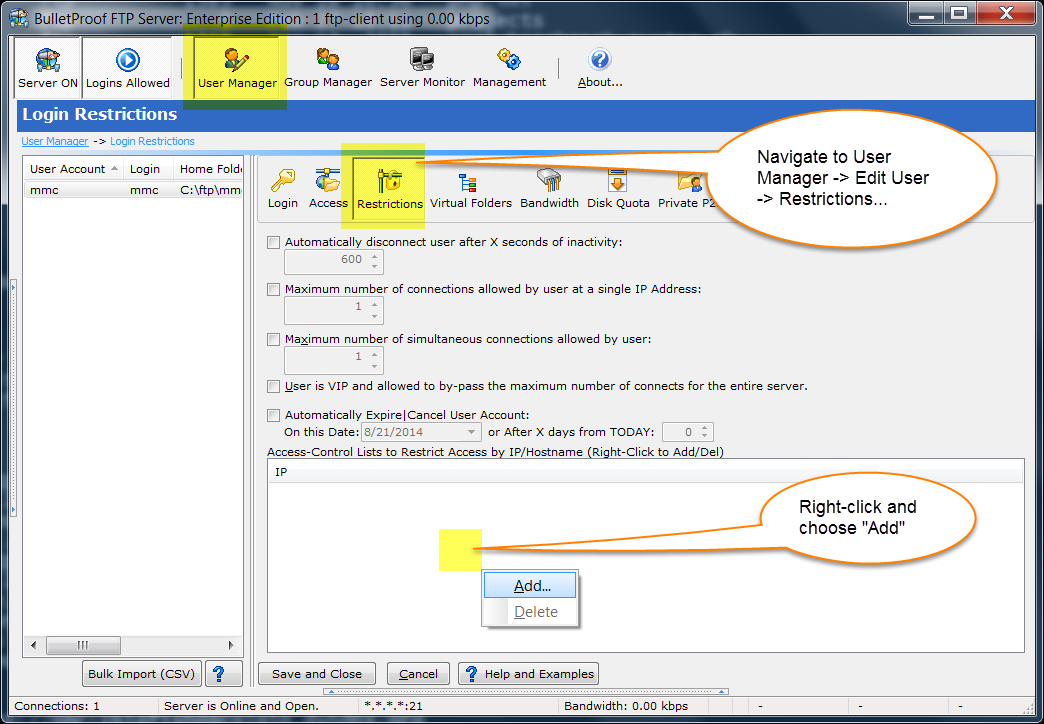
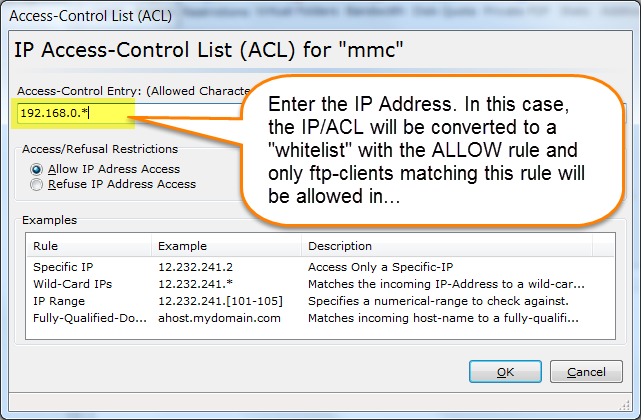
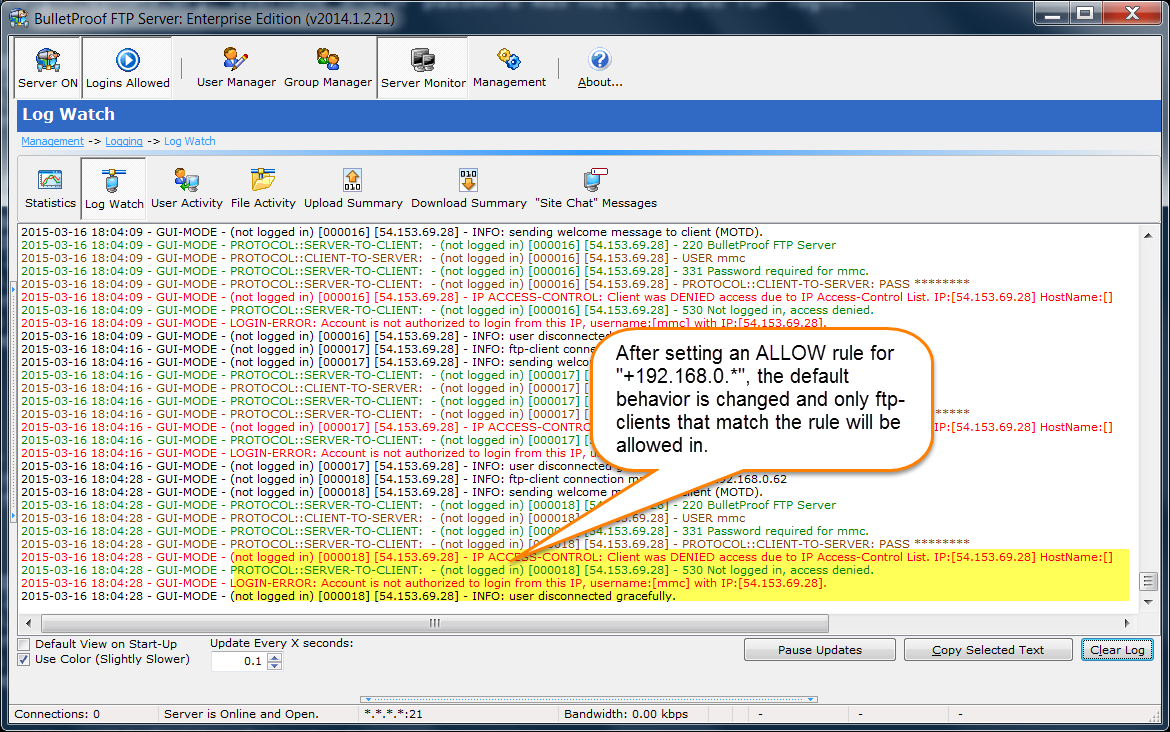
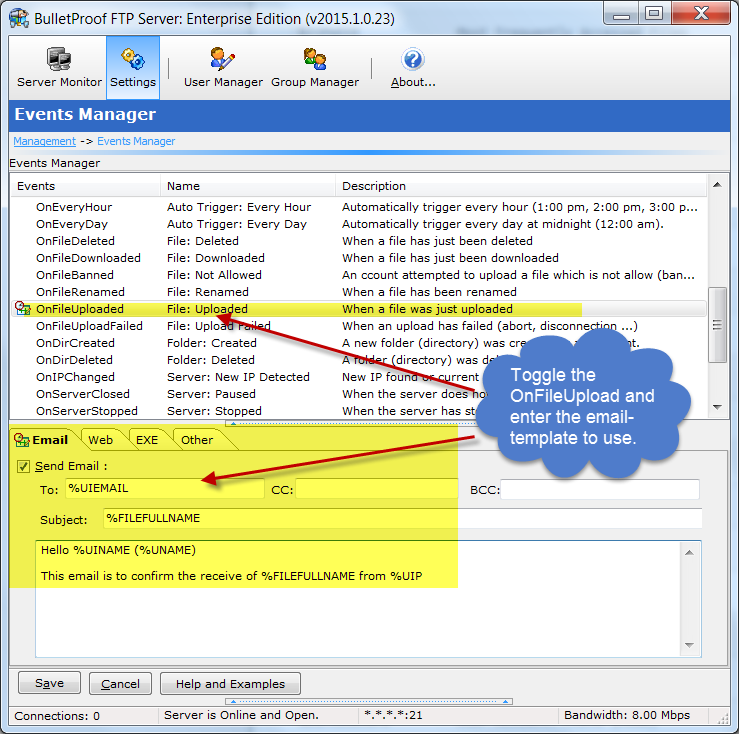
Thank you for your interest in BulletProof FTP Server.
Below is a list of HOWTO articles that have been written over the years to help customers in getting up and running with BulletProof FTP Server.
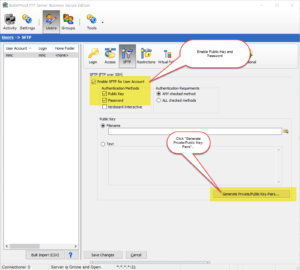
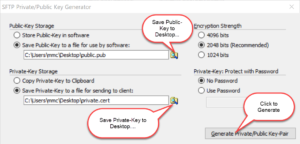
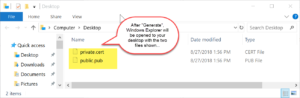
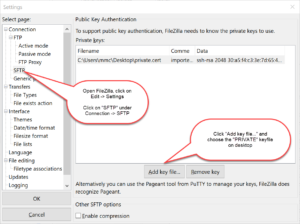
Note: Some of the screen-shots show older versions of the software. The UI hasn’t changed much between different versions, but you might find some of the buttons labeled differently than what appears.
Download, Install and Adding First User
HOWTO: Downloading BPFTP Server 2010
http://blog.builtbp.com/2010/09/howto-downloading-bpftp-server-2010/
HOWTO: Installing BPFTP Server 2010
http://blog.builtbp.com/2010/09/howto-installing-bpftp-server-2010/
HOWTO: Adding a User
http://blog.builtbp.com/2010/09/howto-adding-a-user/
Opening Your Firewall
It’s VERY common that people think only one-port is needed for ftp (default: tcp/ip 21). However, this is not true.
FTP requires at least two ports, one for the control-port (used to login and issue commands, default tcp/ip 21) and a data-port (default tcp/ip 30000 to 30100). One data-port is needed for every concurrent data-connection, for this reason we suggest using a range of 100 ports which will handle most needs.
HOWTO: Windows Firewall and BPFTP Server 2011
http://blog.builtbp.com/2011/06/windows-firewall-and-bulletproof-ftp-server/
HOWTO: Windows Firewall
http://blog.builtbp.com/2010/09/howto-windows-firewall/
HOWTO: Setting up NAT/Passive/Firewall Support
http://blog.builtbp.com/2010/09/howto-setting-up-natpassivefirewall-support/
Licensing
HOWTO: Enter Your Subscription-Code
http://blog.builtbp.com/2013/05/howto-enter-your-subscription-code/
HOWTO: Purchase an Upgrade to your License
http://blog.builtbp.com/2014/02/howto-purchase-an-upgrade-to-your-license/
HOWTO: Remove Your License-Code
http://blog.builtbp.com/2013/05/howto-remove-your-license-code/
Upgrading
FAQ: Can I Upgrade and retain all my Users, Groups and Settings?
http://blog.builtbp.com/2011/12/faq-can-i-upgrade-and-retail-all-my-users-groups-and-settings/
FAQ: Where does BPFTP Server store the Users, Groups and Settings?
http://blog.builtbp.com/2011/12/faq-where-does-bpftp-server-store-the-users-groups-and-settings/
HOWTO: Overridding the Storage-Path for Settings, Users and Groups
http://blog.builtbp.com/2011/10/howto-override-storage-path-for-settings-users-and-groups/
Windows System Service
HOWTO: Windows System-Service
http://blog.builtbp.com/2011/09/howto-windows-system-service/